While it might seem like company databases are filled with mundane files, hackers know the harsh reality. According to Verizon’s Data Breach Investigations Report, the culprits behind cyber attacks come from various corners – outsiders, insiders, company partners, organized crime groups, and affiliated parties.
Here’s a closer look at the percentages for each category:
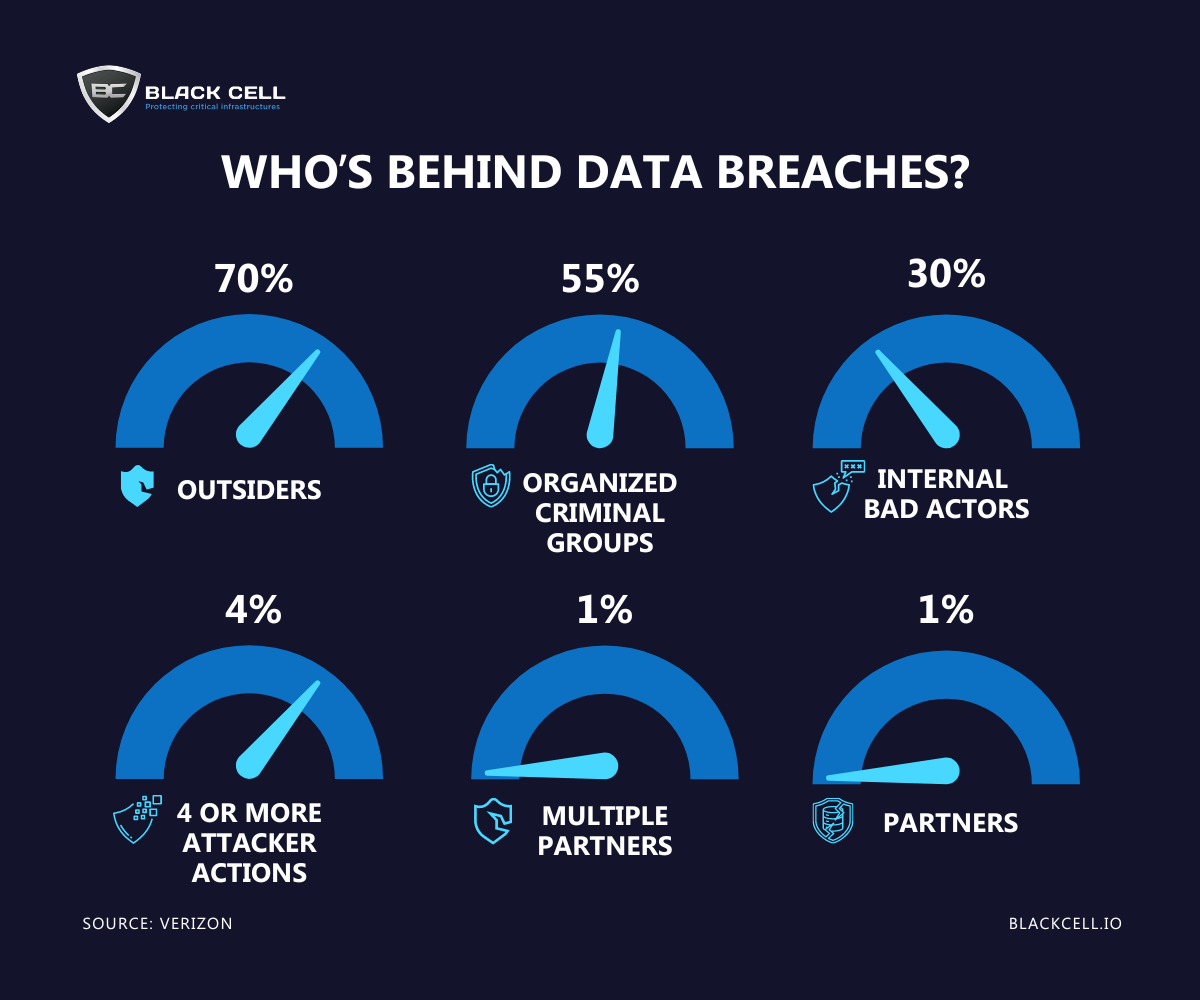
Source: Embroker, Verizon
Author

Péter Szöllősi
OFFENSIVE SECURITY MANAGER
Peter has been the Head of Offensive Security at Black Cell for five years, where he manages the pentester team responsible for providing high-quality ethical hacking services to clients to enhance their security posture. He also contributes to the maintenance and improvement of Black Cell’s security posture with internal and external audits.
Related Posts
The Anatomy of a Phishing Email
Phishing emails remain one of the most effective methods cybercriminals use to steal information....
7 Shocking Cybersecurity Myths That Are Putting Your Business at Risk — And What You Need to Know to Stay Safe
When it comes to cybersecurity, misinformation can be just as dangerous as a real hacker lurking...